Archive for the ‘blogging’ Category
Price of Wireless IDS/IPS
I realize that it has been almost a week since I posted new content on WiFiJedi.com – don’t despair! Over the last week, I wrote two guest posts for other notable blogs.
Last Wednesday, I made another post to my Computerworld blog (“Cautiously Cutting the Cord”) entitled “RSA Inspired Thoughts on Wireless Security”. The post spoke about different Wireless Intrusion Detection System (WIDS) designs. I just started blogging for Computerworld last month and that is my third post – please visit those posts, Digg them (if you think they are worthy), and comment – I love the conversations generated by comments!
Last Thursday, I wrote a blog post on CWNP.com addressing pricing concerns of 802.11n networks. The article had sections outlining the costs and benefits of 802.11n networks. It even had a section titled “WWWBD? (What Would Warren Buffett Do?).
I was actually going to summarize these posts on WiFiJedi.com over the weekend, but I ran into a technical difficulty. I originally typed out this post using the WordPress application for my iPhone while on a flight from Phoenix to Seattle. Since I was on a flight, I had to save it in the “local drafts” folder of the iPhone app. However, when I went back to publish the post, the information wasn’t there! I Googled the issue, and found out that this was a known (and fairly common) issue with the iPhone application for WordPress. The recommended “fix” was to uninstall and reinstall the application. While this method didn’t allow me to recover the data I had already drafted, it did seem to remedy the issue. Just to be sure, I wrote a test post, saved it to the local drafts, and came back later and pushed it to the WordPress website.
Lastly, if you can’t get enough discussion of RSA, WIDS/WIPS, and Pricing, you can check out Joanie Wexler’s Network World article on “How intrusion prevention costs compare”. Happy reading!
Do You Squidoo?
 I recently created a web page (called a “lens”) on Squidoo. Squidoo allows people to create a lens on what they are passionate about. Therefore, my Squidoo lens is on Wireless Networking & Security!
I recently created a web page (called a “lens”) on Squidoo. Squidoo allows people to create a lens on what they are passionate about. Therefore, my Squidoo lens is on Wireless Networking & Security!
Squidoo was a site that was, in-part, created by Seth Godin (the author). I also have Seth’s Blog in my blogroll on the left-hand side of WiFiJedi.com
I don’t want to spoil the actual content, but I will give you a few clues as to what’s on my lens – text modules, YouTube videos, ties to Twitter streams, links to some of my favorite books on Amazon, etc. Go see for yourself!
You can check out my Squidoo lens at http://www.squidoo.com/wifijedi
Don’t forget to find my other cross-linked content:
My LinkedIn profile – http://www.linkedin.com/douglashaider
My Twitter stream – http://www.twitter.com/wifijedi
Insider’s Guide to a SANS Conference – Setup
This is the first blog post in a series, “Insider’s Guide to a SANS Conference”. It corresponds to my attendance at the SANS Phoenix Conference March 23-30, 2009.
As a disclaimer, this “Insider’s Guide” will not provide you confidential information.
Also, you should know that I am “nobody special” within the organization. This is the third conference I have attended, all through their work-study (volunteer) program. I have Mentored the wireless course and taught a wireless Stay Sharp course in Dallas a couple years ago, but that’s it.
The series is meant to be detailed description of my participation and to hopefully encourage others to attend. (I am a big fan!) I am taking the “Security Leadership Essentials for Managers” course, which is being taught by Stephen Northcutt – the CEO of SANS.
I am also “micro-blogging” about the conference via Twitter. You can find my updates with the hashtag #SANS_PHX …better yet, you can “follow me” on Twitter @wifijedi to see all the updates in your own time line!
Today the conference organizers & volunteers set up the conference. Since this is a smaller, regional conference, there are only 5 volunteers (one for each course they are running). Setting up consisted of the following activities:
- Preparing name badges
- Preparing registration folders
- Recieving and sorting courseware (books)
- Stuffing totes with courseware and other inserts
- Sorting conference shirt by size
- Placing signage throughout facility directing attendees to registration, classrooms, internet cafe, etc.
- Setting up registration station
- Preparing course evaluation forms & folders
- A briefing regarding volunteer duties & expectations
- Etc.
I am looking forward to seeing all the attendees at the registration booth from 7:00 – 9:00 AM tomorrow morning!
Related Posts:
Check out my updated sidebar!
There are a couple new features to my blog’s sidebar. Go ahead. Look left. You’ll see them there. 🙂
The first is the following row of graphics:
These are meant to make it easy to share WiFiJedi.com with your friends & family (and complete strangers). Included are links to SlashDot, Digg, Reddit, Del.icio.us, Facebook, Technorati, and StumbleUpon. I really appreciate any votes of confidence that you submit to these websites!
Just beneath that set of graphics, you will see an expanded set of links, which now includes my BlogRoll. For those that are fairly new to blogs & blogging, a blog roll is simply a list of my favorite blogs. Feel free to suggest other blogs (particularily those about wireless networking & security) within the comments section of this post!
Lastly, I wanted to let you know that I really getting more involved with Twitter. This seems to be a great micro-blogging and communication tool where I have barely scratched the surface. You can “follow me” @wifijedi
Can IT Vendors be Objective?
Here is another guest post that I wrote for An Information Security Place. This is something that I am worked up about, so I am re-publishing it here to maximize the audience. 🙂
————————————————————————————
Can IT Vendors truly be objective? Or does everything they say have to be viewed through a lens of “they are trying to sell me something”?
Join me while I rant…
Personally, I think IT vendors can be objective.
Sure, we manufacture and sell things…
*Gasp* – We even profit from selling.
But that doesn’t mean we can’t be objective.
i.e. – I try to provide solid vendor-neutral information to the wireless community through my blog, http://wifijeidi.com.
(In fact, only 2 of the nearly 40 blog posts I have completed to-date have been about my employer, Xirrus.)
However, not everyone sees it that way.
Let me give you an example…
I requested press access to an industry event as a blogger.
However, I was told that I can’t get a pass of this nature because I work for a vendor.
Furthermore, I was told that bloggers of major publications (ComputerWorld, Network World, ZDNet, etc.) would qualify.
So I went out seeking a spot with one of these publications as one of their bloggers.
(I even had a solid lead directly to an editor with a reference from another well know blogger at one of these publications.)
However, I was turned down again. Because I work for a vendor.
My “commentary”…
Presumably, working for a vendor means that I can’t be objective. Which I personally think is %^&$*&!
Let’s take a look at some profiles of bloggers who have been picked up by these publications. I would like to take a closer look at two common blogger profiles: Value Added Resellers (VARs) and Independent Consultants.
I have noticed that if you work for a VAR, you can blog for major publications. Correct me if I am wrong – as a VAR, don’t you sell some vendor’s equipment, but not others? It would seem to me, in that position, it is possible to have nuances or conflicting agendas. At least working for a manufacturer, you know where my “official” loyalties are.
Other common profile for bloggers on these publications is that of an “independent” consultant. I would think a large portion of their livelihood depends on their ability to provide consulting services. If that’s the case, don’t you think they would blog about things that (at least indirectly) drive their own business? After all, their financial success is directly tied to the success of a single person – themselves. Working for a manufacturer (or any large organization) mitigates this factor because my financial situation is determined by the success of the group, and not by what I do or say to drive my own consulting business.
This isn’t intended as an attack on publications or their bloggers, just an honest discussion of how they can be objective, but somehow it is perceived that I can’t. What about my credentials?!?
Besides working for a vendor (for several months), I have also worked as a consultant and auditor (for many years). I hold over a dozen IT certifications, ALL of which are vendor-neutral. On my LinkedIn profile, I have the coveted “500+ connections”, many of who are employed by my competition – Aruba, Meru, Motorola, etc. I started my blog to serve as a thought leader and I am a frequent speaker at industry events, professional organization meetings, and universities.
If you know someone at an IT publication that is willing to have me as a wireless networking and security blogger, have them contact me at douglas.haider@xirrus.com
Wait, I had better not use my corporate email address. That might signal I can’t be objective. 🙂
Instead, have them contact me at douglashaider@hotmail.com
An Information Security Place
If you are wondering why I didn’t post yesterday, it is because I served as a guest author on another blog, An Information Security Place. This blog was created by a friend and former colleague of mine, Michael Farnum. It is *really* popular – you should check it out! How popular do you ask? Well, if you type “an information security place” into the main page of Google, you will get approx. 25 million results. That is pretty impressive, considering the terms “802.11n” and “WiFi hotspots” only return approx. 12 million results combined.
My post yesterday was titled Factors Determing Installed WLAN Quality, and came out of a phone conversation that I had with Veriwave’s CTO and VP of Marketing earlier in the week. We spoke about the focus on wireless coverage and low interference when field testing WLANs. At a high level, we all agreed there were many other factors to consider, shown in the chart below:
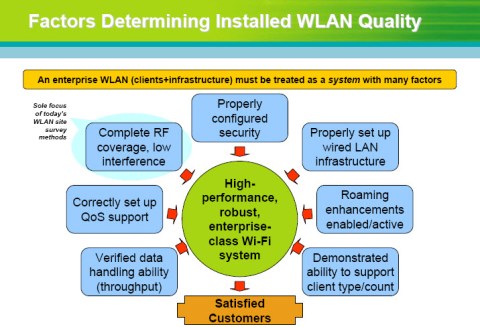
Factors Determining Installed WLAN Quality
Check out the post at An Information Security Place. Happy Reading!
 Leave a comment
Leave a comment Are you one of the thousands of people who already read,
Are you one of the thousands of people who already read, 


![[LinkedIn]](https://i0.wp.com/farm4.static.flickr.com/3477/3463037125_247575d1f3_m.jpg)
![[LinkedIn]](https://i0.wp.com/farm4.static.flickr.com/3598/3463037145_924738ec38_m.jpg)
You must be logged in to post a comment.